Azure AD Connect Cloud Sync Agent and Intune 'Hybrid' Enrollment
Domain joined devices, Azure AD Connect Cloud Sync agent, and Intune enrollment. All three things I had to deal with recently in an environment that was going through a cloud scentric migration. I had a fun time going through all the weird things that come with the below solution.
I do want to state this as a disclaimer: The solution below to my knowledge is not documented and possibly not supported. I would only recommend doing this if you are in the same scenario described below.
Introduction
In this particular environment they have not used Intune before and were in a traditional domain joined environment and because of some other reasons, a hybrid/mobile workforce. These problems are not unknown from others in most environments since they most likely have done this over the pandemic.
Now domain joined devices, VPN, and Intune can definetly work. As well as the methods described in Microsoft’s enrollment methods. These usually fall upon the Azure AD Connect installation on a server do to the password hash sync, hybrid join, etc. Easy, done it before, could do it again.
Now the Azure AD Connect Cloud Sync Agent is completely different that the Azure AD Connect installation that is more common. This agent “get’s the job done” when talking about user accounts and keeping them in sync. Where this differs is that it can’t do Hybrid Azure AD Join for devices. Well atleast documented and supported.
Typically, I would throw the GPO and apply it to the device and let everything go, but Azure AD Connect Cloud Sync can’t do that natively. So back to the drawing board.
Drawing Board
GPO isn’t going to work, what can I use?
- Manual Enrollment
- New Azure AD Joined Device
- Provisioning Package
Manual Enrollment
I want to use this as a last result. One because users will never do this and follow directions without some help. Resulting in more help desk calls and tickets.
New Azure AD Joined Device
While inventory is getting better for devices and is currently setup in this environment this would be a bit a logistical mess. This isn’t a great option as well.
Provisioning Packages
While Microsoft documents provisioning packages as a method to setup devices straight out of the box for bulk enrollment. I think I can make this work for just enrollment into Intune. I can also automate this using PowerShell. Let’s go down this route.
Working with Provisioning Packages
To get started with Provisioning Packages you need the Windows Configuration Designer application. I recently found that it is in the Microsoft Store. Below is what we are going to need.
Next we are going to click into Provision Desktop Devices
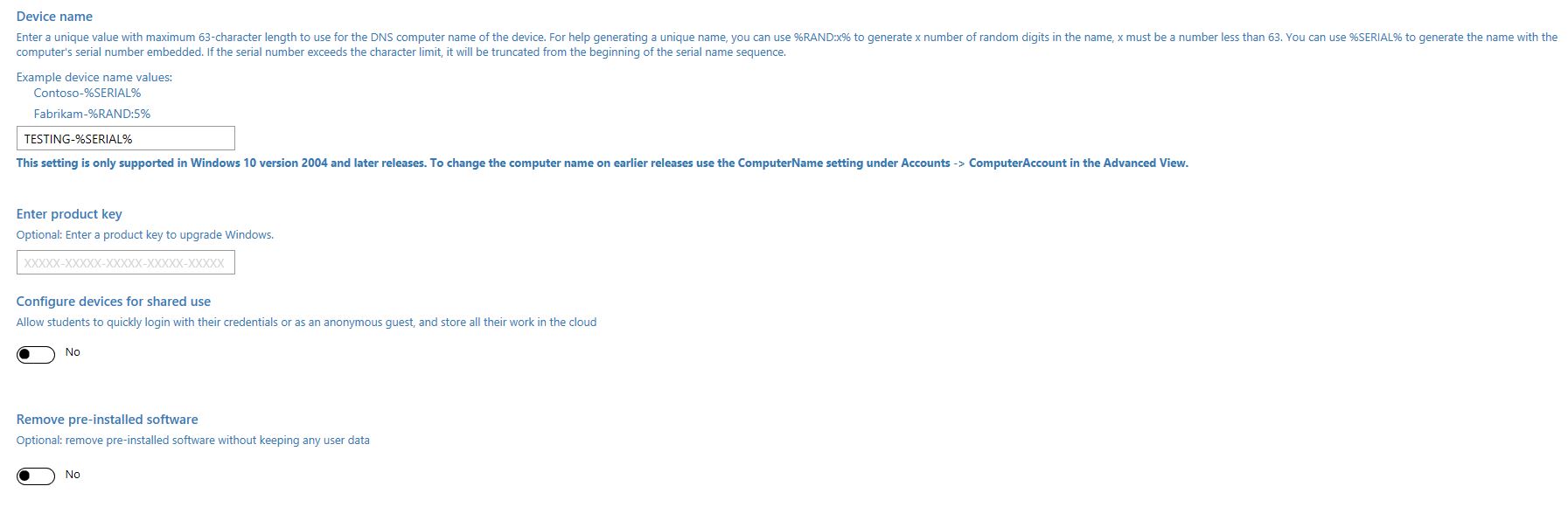
Give it a name for the project. It doesn’t matter what you chose here.
The next screen below, you want to leave blank except for the name. We need that for the Windows Configuration Designer to say its a valid package.
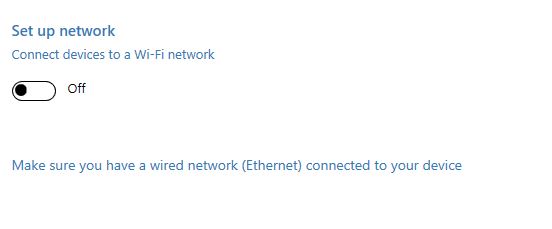
Don’t give it a Wi-Fi to connect to.
Next, we need to work with bulk enrollment and get the token. The two things you need are to change to Azure AD and then click Get Bulk Token. This will take you through some prompts to get the token to do the Intune enrollment.

Then click through the rest and click finish to compile the two files needed.
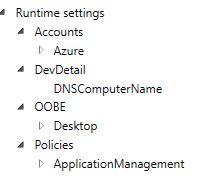
Now before you close, in the bottom left there is an advanced editor. We want to go into there.
In there on the right there is a Runtime Settings. We want to delete, DevDetail, OOBE, and Polices. Since we don’t need those. All we need is the Accounts.
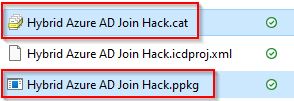
Save the project and export and create the package from the upper menu bar.
You will want to get the .ppkg and .cat files since those are needed for provisioning.
PowerShell
We now have the .ppkg and .cat files needed to enroll and you can manually install these on devices one by one, but I don’t have the time for that. PowerShell to the rescue with some help from an RMM agent to push it out. You can use anything that will run a PowerShell script, but personally have devices all over so this was the best and easiest method.
|
|
The Finale
When you push that to devices, the ppkg file will enroll using the bulk enrollment method (sadly no user affinity). The device will get the Intune Management Extension and I found a reboot is necessary eventually to have it show in Intune (at least I was being impatient).
Again, this isn’t pretty or the recommended way to enroll, but this was the best I could think of in this unique environment.