Entra ID and Intune: Viewing Logins Remotely for Entra ID Joined Devices
I came across an scenario I wouldn’t think I was going to need to find a solution, but it really isn’t a problem that is typically common this day in age.
Problem: A lost device that is needs to be found. How can I track down who had it last?
Assumptions
- Device isn’t necessarily lost. Maybe displaced.
- It hasn’t been on to check in with Intune.
- In my case, I am assuming it isn’t wiped.
- Device is captured in Entra ID under Sign In Logs for a particular sign in session.
- The device is a shared device and you only know the computer name.
What Does Entra ID Show?
Entra ID oddly enough doesn’t show the column of the device information. Not a Device ID or hostname. Entra ID doesn’t even let you use it as a filter in the user interface.

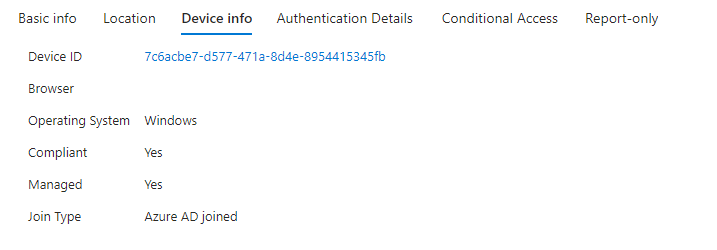
As you can see, not as easy as you might think. Let’s see how we can get that information in a more readable format to tell more of a timeline of the sign ins from a Entra ID Joined Device.
Graph API to the Rescue!
We are going to leverage the Get-MgAuditLogSignIn command under the Microsoft.Graph.Reports PowerShell module.
First, lets install and import the module we are going to need. I installed all the Graph Modules since I didn’t have them. You may already have them installed.
|
|
Let’s authenticate with the correct rights to play nice.
|
|
Next, why don’t we peak to see what an example return is like.
|
|
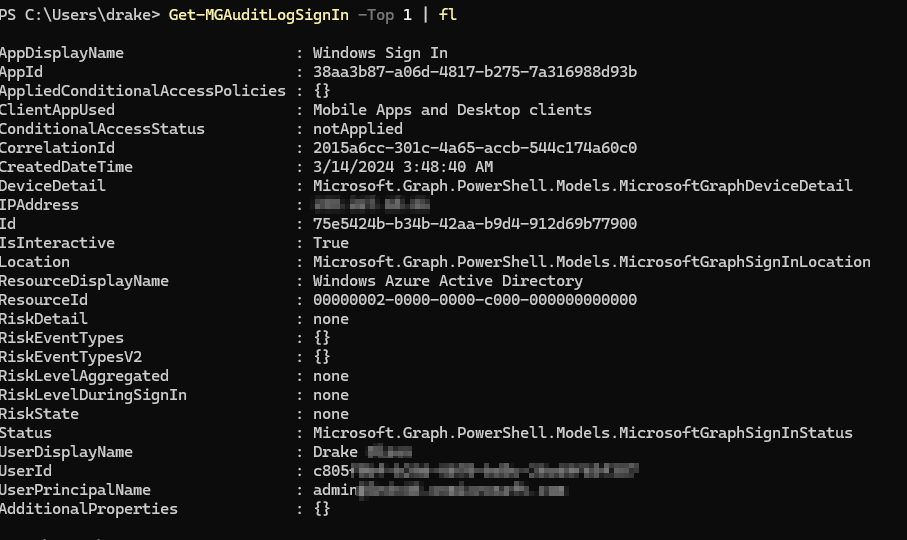
You can see we have a response back, and luckily this is my test environment and my app name is Windows Sign In. That’s is actually the one we are going to look at. We also get back device details, user properties and more that we couldn’t see very easily in the Entra ID Sign In log table.
Let’s narrow down to Windows Sign In only and store the response so we can see the properties. This may take a little bit, but we’ll fix that later.
|
|
Let’s acutally dive into the device properties from the sign in.
|
|
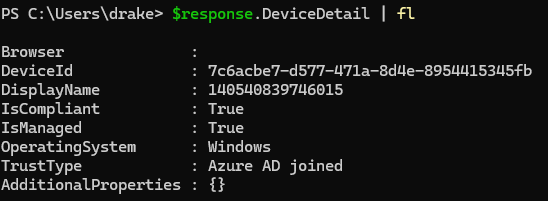
So we can see that we get the DeviceId, DisplayName, and much more. With this information we can now send this in a somewhat of a loop to get the sign in history of the device if we would like. Make sure to replace your display name with the computer’s hostname you are looking for. I also hard coded the number of days to look back from.
|
|
With running this script, I get the output below.
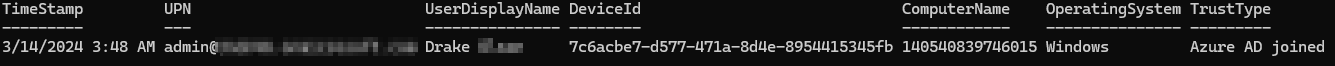
Note: The time in this is not localized.
This is exactly, what I am looking for! I can now send this and start tracking down that device first by starting with who signed into the device last. I would still recommend at somepoint that you send a wipe command to the device just in case, it does end up stolen!
Resources
Petri example was used to see how you do it previously using the AzureADPreview PowerShell module.
Microsoft Docs was used to see if the commands changed a bit from AzureADPreview to Microsoft.Graph.Reports